In the fast-evolving landscape of digital transactions and decentralized systems, the importance of blockchain security cannot be overstated. Blockchain, initially designed as the underlying technology for cryptocurrencies like Bitcoin, has now transcended its origins to become a transformative force in various industries. As organizations increasingly rely on blockchain technology to streamline processes, enhance transparency, and ensure trust in digital interactions, the need for robust security measures has become a paramount concern.
Blockchain, at its core, is a distributed ledger that records transactions across a network of computers. The decentralized nature of this technology eliminates the need for a central authority, offering unparalleled transparency and immutability. However, the open and transparent nature of blockchain also makes it a target for malicious actors seeking vulnerabilities to exploit.
The importance of blockchain security lies in safeguarding the integrity and confidentiality of data stored on the blockchain. Whether it involves financial transactions, blockchain in supply chain information, or sensitive personal data, the secure functioning of blockchain systems is vital to maintaining trust among users. Any compromise in security could lead to severe consequences, including financial losses, privacy breaches, and damage to an organization’s reputation.
Blockchain technology has witnessed a rapid proliferation beyond its initial use in cryptocurrencies. Industries such as finance, healthcare, supply chain, and more are integrating blockchain to enhance efficiency and accountability. The decentralized and tamper-resistant nature of blockchain makes it an ideal solution for mitigating fraud, reducing intermediaries, and ensuring the integrity of digital records.
How Do Blockchain Security Testing Tools Play a Vital Role in Identifying Vulnerabilities within Decentralized Networks?
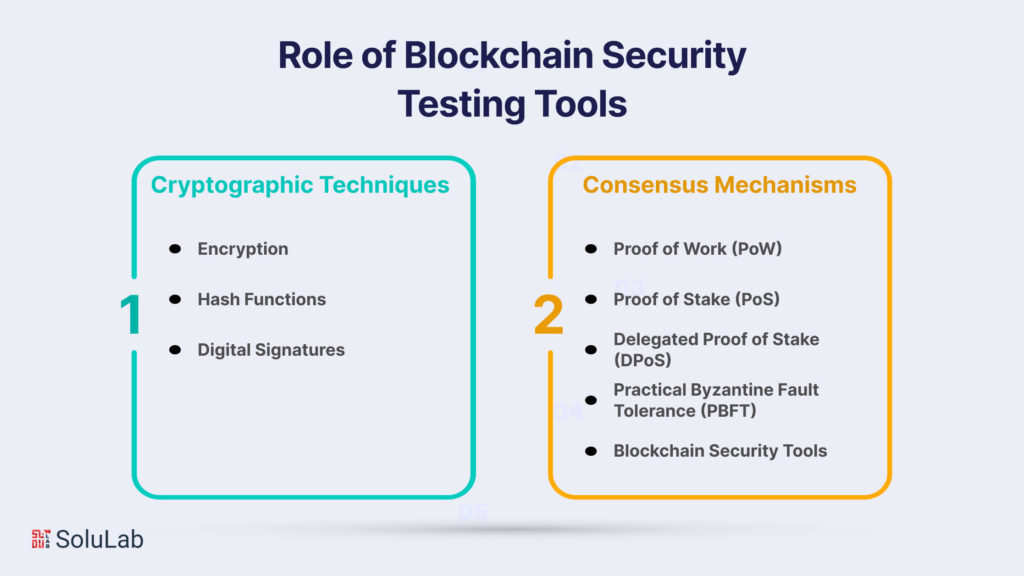
Blockchain, as a revolutionary technology, has reshaped industries and introduced a new paradigm for secure and transparent transactions. However, ensuring the security of blockchain systems is paramount to maintaining trust and integrity in decentralized networks. In this exploration of Blockchain Security Fundamentals, we delve into the cryptographic techniques and consensus mechanisms that form the bedrock of blockchain security.
A. Cryptographic Techniques
-
Encryption
Encryption is the cornerstone of blockchain security, ensuring that sensitive data remains confidential and tamper-proof. Utilizing advanced cryptographic algorithms, blockchain systems encrypt transaction data, making it nearly impossible for unauthorized parties to access or alter information. This robust encryption is pivotal in safeguarding the privacy and integrity of transactions across the blockchain.
-
Hash Functions
Hash functions play a crucial role in blockchain security by generating unique, fixed-size hash codes for data blocks. These one-way functions ensure data integrity, as even the slightest modification to the original data results in a completely different hash. Blockchain employs hash functions to create a chain of blocks, linking them securely and providing an immutable record of transactions.
-
Digital Signatures
Digital signatures authenticate the origin and integrity of transactions in blockchain networks. Using asymmetric cryptography, digital signatures verify the identity of the sender and ensure that the transaction has not been tampered with during transmission. This cryptographic technique enhances the trustworthiness of blockchain transactions, bolstering the overall security of the system.
B. Consensus Mechanisms
-
Proof of Work (PoW)
PoW, the original consensus mechanism, requires participants (miners) to solve complex mathematical puzzles to validate transactions and add blocks to the blockchain. This energy-intensive process ensures the security and decentralization of the network by making malicious attacks economically unfeasible.
-
Proof of Stake (PoS)
PoS replaces the energy-intensive PoW with a system where validators are chosen to create blocks based on the amount of cryptocurrency they hold and are willing to “stake.” PoS enhances efficiency and reduces environmental impact, while still maintaining a robust level of security against malicious actors.
-
Delegated Proof of Stake (DPoS)
DPoS introduces a democratic element to the consensus process by allowing token holders to vote for a limited number of delegates who have the authority to validate transactions and create blocks. This system enhances scalability and efficiency while maintaining a high level of security through the democratic selection of trustworthy delegates.
-
Practical Byzantine Fault Tolerance (PBFT)
PBFT is a consensus mechanism that prioritizes speed and efficiency. Utilizing a predetermined set of nodes to reach consensus, PBFT ensures security in a permissioned blockchain environment. The system can withstand a certain number of faulty nodes without compromising the overall security and reliability of the blockchain.
Related: Decentralized Physical Infrastructure Networks (DePIN)
-
Blockchain Security Tools
To fortify the security of blockchain networks, various blockchain security testing tools and general security tools for blockchain have emerged. These tools encompass vulnerability scanners, penetration testing frameworks, and smart contract auditors. Security-conscious organizations often leverage these tools to identify and address potential weaknesses in their blockchain implementations, ensuring a resilient and secure decentralized infrastructure.
What are Threats to Blockchain Security?
Blockchain technology, heralded for its decentralized and secure nature, is not immune to threats. As the adoption of blockchain continues to rise, so does the need to address potential vulnerabilities. Several threats to blockchain security demand attention, each posing unique challenges to the integrity and trustworthiness of the decentralized ledger system.
-
51% Attacks
A 51% attack occurs when a single entity or a group controls more than 50% of a blockchain network’s computing power. This dominance enables malicious actors to manipulate transactions, potentially leading to double-spending. To mitigate this threat, blockchain security tools such as consensus algorithms and monitoring solutions are crucial. These tools ensure the distribution of power across the network, preventing any single entity from gaining excessive control.
-
Double-spending
Double-spending is a concern where a user spends the same cryptocurrency more than once. This threat undermines the fundamental principle of blockchain, which relies on consensus to validate transactions. Security tools for blockchain, including robust consensus algorithms like Proof of Work (PoW) or Proof of Stake (PoS), play a pivotal role in preventing double-spending attacks by ensuring transparent and verifiable transaction histories.
-
Sybil Attacks
Sybil attacks involve creating multiple fake identities to gain control over a network. This threat exploits the decentralized and pseudonymous nature of blockchain. Employing blockchain security testing tools is crucial to identify and prevent Sybil attacks. These tools help detect anomalies in node behavior, ensuring that each node in the network represents a unique and legitimate participant.
-
Smart Contract Vulnerabilities
Smart contracts, while enhancing blockchain functionality, can harbor vulnerabilities that compromise security. Security tools for blockchain, specifically designed for smart contract auditing, are essential. These tools thoroughly analyze code for potential weaknesses, ensuring that smart contracts execute as intended and are resistant to exploitation.
-
Malicious Nodes
The decentralized nature of blockchain involves various nodes validating transactions. However, malicious nodes can compromise the network’s security. Blockchain security testing tools come into play here by constantly monitoring node behavior and promptly identifying any deviations from normal patterns. This proactive approach helps maintain the network’s integrity and prevents unauthorized access.
-
Regulatory and Compliance Challenges
Beyond technical threats, blockchain faces challenges related to regulatory and compliance issues. Navigating the evolving landscape of regulations demands specialized blockchain security tools. These tools assist organizations in ensuring that their blockchain implementations comply with legal frameworks, protecting against potential legal repercussions.
What are the Blockchain Security Tools?
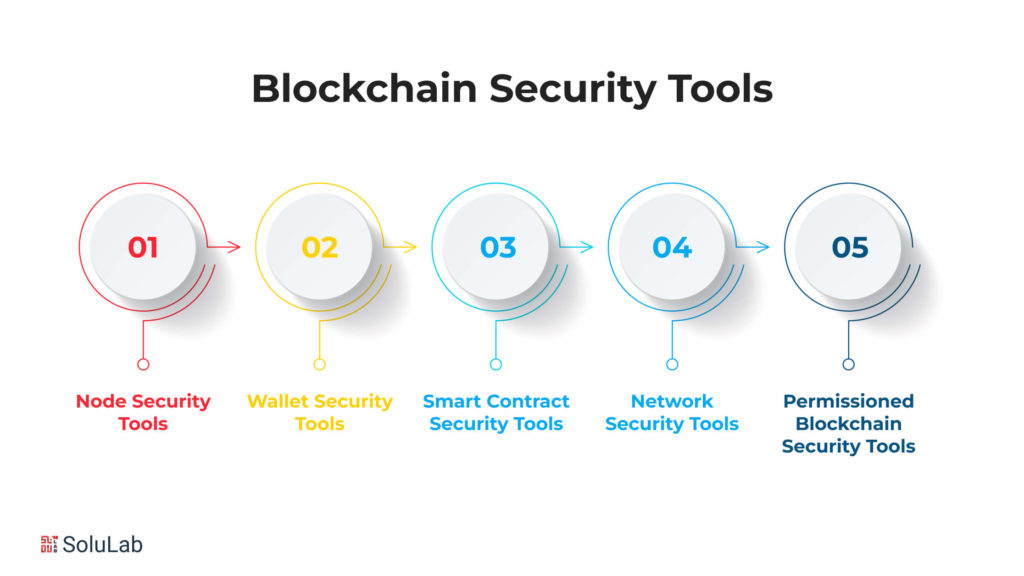
Blockchain technology, with its decentralized and transparent nature, has revolutionized various industries. However, the increasing complexity of blockchain systems has also given rise to security concerns. To address these issues, a variety of specialized tools have emerged, categorized into different segments based on their primary focus.
A. Node Security Tools
-
NodeWatch
NodeWatch is a cutting-edge tool designed to enhance the security of blockchain nodes. It employs advanced monitoring mechanisms to detect unusual activities and potential threats within the node infrastructure. This proactive approach ensures the integrity and reliability of the entire blockchain network.
-
Nodestalker
Nodestalker complements NodeWatch by providing real-time tracking and analysis of node behavior. It employs heuristic algorithms to identify patterns associated with security breaches or suspicious activities. By constantly monitoring nodes, Nodestalker contributes to the early detection and mitigation of potential risks.
B. Wallet Security Tools
-
Ledger Nano S
Ledger Nano S is a hardware wallet designed to secure cryptocurrency holdings. With robust encryption and offline storage capabilities, it ensures that private keys remain isolated from online threats. This tool is an integral part of the arsenal for individuals and businesses seeking reliable wallet security solutions.
-
Trezor
Trezor, another hardware wallet, emphasizes simplicity without compromising security. Its open-source design and PIN protection mechanism make it a preferred choice for users looking to fortify their digital assets. Trezor’s compatibility with various cryptocurrencies adds versatility to its security features.
C. Smart Contract Security Tools
-
MythX
MythX is a powerful security analysis tool for Ethereum smart contracts. It employs a comprehensive set of security checks to identify vulnerabilities and potential exploits. Integrating MythX into the development pipeline enhances the overall security posture of smart contracts, reducing the risk of costly vulnerabilities.
-
Securify
Securify specializes in the formal verification of smart contracts, ensuring they adhere to predefined security specifications. By leveraging formal methods, Securify provides a systematic approach to identifying vulnerabilities and verifying the correctness of smart contract code.
-
Oyente
Oyente focuses on detecting common security issues in Ethereum smart contracts. Its static analysis capabilities enable developers to identify vulnerabilities before deployment. Oyente plays a crucial role in preventing security flaws that could lead to financial losses or exploit opportunities.
D. Network Security Tools
-
Blockscan
Blockscan is a comprehensive network security tool designed for blockchain protocols. It monitors network traffic, identifies potential threats, and ensures the integrity of data transmissions. By proactively addressing network-level vulnerabilities, Blockscan contributes to a more secure and resilient blockchain infrastructure.
-
EtherScan
EtherScan provides real-time monitoring and analysis of the Ethereum blockchain. As a network security tool, it enables users to track transactions, contract interactions, and network statistics. EtherScan’s comprehensive approach aids in identifying and mitigating potential threats to the Ethereum network.
E. Permissioned Blockchain Security Tools
-
Hyperledger Caliper
Hyperledger Caliper focuses on benchmarking the performance and security of permissioned blockchains. Simulating various use cases and stress-testing blockchain networks, helps organizations assess the resilience and security of their permissioned blockchain implementations.
-
Chaincode Security Analyzer
Specifically tailored for Hyperledger Fabric, the Chaincode Security Analyzer scrutinizes chaincode (smart contract) security. It conducts static analysis to identify vulnerabilities, enhancing the overall security posture of Hyperledger Fabric-based permissionless blockchains.
How Can the Incorporation of Blockchain Security Testing Tools Complement the Use of Cryptographic Tools?
Blockchain technology has revolutionized various industries by providing a decentralized and secure framework for transactions. As the popularity of blockchain grows, so does the need for robust security measures. Cryptographic tools play a pivotal role in ensuring the integrity and confidentiality of blockchain networks. In this article, we will explore key cryptographic tools, including OpenSSL, HashiCorp Vault, and Amazon Key Management Service (KMS), that play a crucial role in bolstering blockchain security.
A. OpenSSL for Blockchain Security
OpenSSL stands out as a widely used open-source toolkit for implementing cryptographic protocols in various applications, including blockchain. Its versatile nature allows developers to integrate SSL/TLS protocols, cryptographic algorithms, and key management functionalities into their blockchain applications seamlessly. OpenSSL ensures secure communication and data integrity, making it an indispensable tool for blockchain security.
B. Key Management Tools
-
HashiCorp Vault
Key management is a critical aspect of blockchain security, and HashiCorp Vault is at the forefront of providing a robust solution. Vault offers a centralized platform for managing cryptographic keys, secrets, and sensitive data securely. With features like dynamic secret generation and rotation, HashiCorp Vault minimizes the risk of unauthorized access and strengthens the overall security posture of blockchain networks.
-
Amazon Key Management Service (KMS)
Amazon KMS is a cloud-based key management tool that integrates seamlessly with blockchain applications hosted on the AWS platform. It provides a scalable and secure solution for creating, storing, and controlling cryptographic keys. With features like key rotation and audit trails, Amazon KMS enhances the security of blockchain applications, ensuring that cryptographic keys are managed effectively and in compliance with industry standards.
How does its Automated Scanning Contribute to the Security of Decentralized Applications?
In the dynamic landscape of blockchain technology, ensuring the security and integrity of decentralized networks is paramount. Various monitoring and auditing tools have emerged to address the unique challenges posed by the blockchain ecosystem. This article explores two categories of such tools: Security Auditing Platforms and Blockchain Network Monitoring Tools.
A. Security Auditing Platforms
-
Quantstamp
Quantstamp stands out as a leading security auditing platform for blockchain systems. Leveraging advanced security analysis techniques, Quantstamp provides comprehensive audits of smart contracts.
Its automated scanning identifies vulnerabilities, ensuring the integrity of decentralized applications (DApps) built on blockchain platforms. Quantstamp plays a crucial role in mitigating risks associated with smart contract vulnerabilities, thereby enhancing the overall security posture of blockchain networks.
-
Certik
Certik specializes in blockchain security through a combination of formal verification and static analysis. It offers a robust platform for auditing smart contracts, identifying vulnerabilities, and ensuring code integrity.
Certik’s approach involves mathematical proofs to validate the correctness of smart contract code, making it a trusted choice for projects seeking a high level of assurance in their blockchain security. The platform contributes significantly to the development of secure and reliable decentralized applications.
B. Blockchain Network Monitoring Tools
-
Chainkit
Chainkit emerges as a powerful blockchain network monitoring tool designed to enhance security and performance. It provides real-time monitoring of blockchain transactions, enabling quick detection of anomalies or suspicious activities.
Chainkit’s capabilities extend to data integrity verification and the identification of potential threats, making it an indispensable tool for maintaining the resilience of blockchain networks. Its user-friendly interface and customizable alerts contribute to efficient blockchain security management.
-
Alethio
Alethio offers comprehensive analytics and monitoring solutions for blockchain networks. Focusing on Ethereum, Alethio provides in-depth insights into network activities, smart contract interactions, and transaction histories.
This tool is instrumental in detecting abnormalities, tracking the flow of assets, and ensuring the overall health of blockchain networks. Alethio’s user-friendly dashboard and customizable reporting make it an invaluable asset for blockchain security professionals.
Conclusion
In conclusion, the Comprehensive List of Blockchain Security Tools presents a robust framework for ensuring the integrity, confidentiality, and availability of blockchain-based systems. These tools play a pivotal role in safeguarding the decentralized nature of blockchain networks, mitigating potential vulnerabilities, and fostering trust among users.
In the realm of blockchain development, SoluLab emerges as a prominent player, offering cutting-edge solutions and expertise in blockchain technology. As a distinguished blockchain development company, SoluLab combines innovative strategies with the utilization of state-of-the-art security tools to create secure and scalable blockchain solutions. Their commitment to excellence is reflected in their ability to address the dynamic challenges associated with blockchain security.
For organizations seeking to bolster their blockchain projects, the option to hire blockchain developers from SoluLab proves to be a strategic move. These skilled professionals bring a wealth of experience and proficiency in leveraging the latest security tools to fortify blockchain applications. By entrusting the development process to SoluLab, businesses can ensure seamless integration of advanced security measures into their blockchain projects.
FAQs
1. What are Blockchain Security Tools?
Blockchain Security Tools are specialized software applications designed to enhance the security of blockchain networks. These tools are crucial for safeguarding digital assets and ensuring the integrity of transactions within the blockchain.
2. How do Blockchain Security Tools contribute to the overall security of a blockchain network?
Blockchain Security Tools play a vital role in identifying and mitigating potential vulnerabilities within the blockchain. They employ advanced techniques to fortify the network against cyber threats, ensuring a robust and secure environment for digital transactions.
3. Why is it essential to use security tools specifically tailored for blockchain development?
Utilizing security tools tailored for blockchain development is crucial because traditional security measures may not address the unique challenges posed by decentralized networks. Specialized tools are designed to counteract threats specific to blockchain technology.
4. How can a blockchain development company benefit from incorporating Blockchain Security Tools into their projects?
Blockchain development companies can significantly enhance the security posture of their projects by integrating specialized security tools. This not only protects their clients’ assets but also builds trust by demonstrating a commitment to robust security practices.
5. Are there specific tools for blockchain security that focus on smart contract auditing?
Yes, certain blockchain security tools specialize in smart contract auditing. These tools thoroughly review and analyze smart contract code, identifying potential vulnerabilities and ensuring the secure execution of smart contracts on the blockchain.