Over time, as technology has advanced, so has the scope of fraudulent acts. Therefore, upholding security regulations is one of the most important duties involved in transaction processing. Even though blockchain technology has emerged as one of the most promising developments, more security requirements are still required to ensure transaction security. Zero Knowledge Proof, or ZKP, is an excellent choice in certain situations.
Blockchain has been linked to cryptography since its conception. That being said, since ZKP was launched, blockchain and cryptography have garnered more interest. To completely safeguard the transaction on a blockchain network, cryptographic techniques are employed. Put differently, the fusion of blockchain technology with encryption has resulted in a safe way to conduct financial transactions.
What is Zero-Knowledge Proof?
With zero knowledge proof of knowledge, no details are disclosed during a transaction other than the exchange of a value that is known to the prover and verification experts (the two ends of the procedure). Zero-knowledge proof is the concept that a person may demonstrate to another user that they are aware of an absolute value without really disclosing any additional or other information.
The following three characteristics are intrinsic to ZKPs:
-
Completeness
The transaction is validated, and the prover is allowed to conduct the transaction ahead of time, according to the completeness property. The person who verifies has the power to give the prover the input he previously sought while the transaction statement is accurate.
-
Reliability
The transaction is accurate and does not relate to any fraudulent cases, according to the soundness property. It implies that the verifier cannot be persuaded in any scenario if the transaction circumstances differ and the assertion is false. The verifier is unable to approve the prover’s request for the inputs in this case or certify the prover.
-
Zero-Knowledge
Other than the present statement and whether or not it is real, the verifier is only allowed access to that information. Private information belonging to other parties shall remain concealed.
Zero-Knowledge Proof Architecture
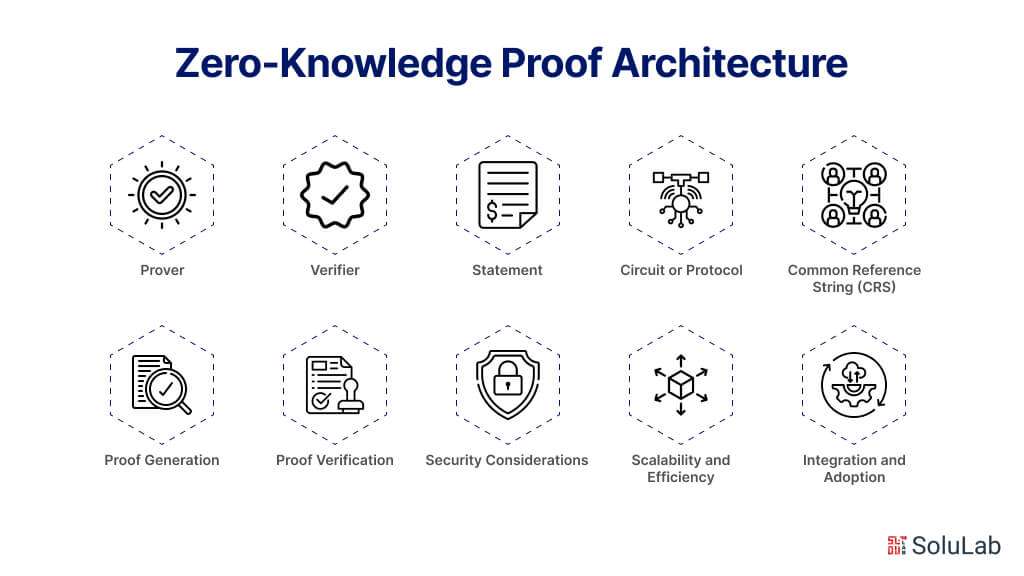
Zero-knowledge proof (ZKP) architecture encompasses the underlying structure, protocols, and components that enable the implementation of zero-knowledge proofs in various applications. The architecture typically consists of several key elements designed to facilitate secure and efficient interactions while preserving privacy and confidentiality. Here’s an overview of the components and considerations within Zero Knowledge architecture:
- Prover: The prover is the entity that wishes to prove the validity of a statement or claim to a verifier without revealing any additional information beyond the truth of the statement. The prover constructs and executes the zero-knowledge proof protocol to convince the verifier of the statement’s validity.
- Verifier: The verifier is the entity that seeks to verify the validity of the statement presented by the prover without gaining any knowledge beyond the statement’s truth. The verifier interacts with the prover during the zero-knowledge proof protocol to validate the statement while maintaining privacy and confidentiality.
- Statement: The statement is the assertion or claim that the prover seeks to prove to the verifier. This could be anything from the correctness of a cryptographic transaction to the possession of certain credentials or attributes. The statement must be formulated in a way that allows for efficient and secure verification using zero-knowledge proofs.
- Circuit or Protocol: The circuit or protocol represents the computational process or algorithm used to encode the statement and generate the zero-knowledge proof. This could involve cryptographic primitives such as hash functions, encryption schemes, or commitment schemes, as well as specific zero-knowledge proof protocols like zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) or zk-STARKs (Zero-Knowledge Scalable Transparent ARguments of Knowledge).
- Common Reference String (CRS): In some zero-knowledge proof systems, a common reference string is generated and shared between the prover and verifier to facilitate the proof generation and verification process. The CRS typically contains random parameters used in the proof generation and is assumed to be generated honestly by a trusted party.
- Proof Generation: The prover generates the zero-knowledge proof using the statement, circuit, protocol, and possibly the common reference string. The proof generation process involves executing cryptographic computations to create a succinct and convincing proof that the statement is true, without revealing any additional information about the statement itself.
Read Blog: Top 10 Layer 1 Blockchain in 2024
- Proof Verification: The verifier verifies the zero-knowledge proof provided by the prover to determine the validity of the statement. The verification process involves executing cryptographic checks to ensure that the proof is valid and corresponds to a truthful statement. If the verification is successful, the verifier accepts the proof without gaining any knowledge beyond the statement’s truth.
- Security Considerations: ZKP architecture includes various security considerations to ensure the confidentiality, integrity, and authenticity of the zero-knowledge-proof system. This involves analyzing potential attack vectors, ensuring cryptographic primitives are secure, and implementing measures to prevent adversaries from compromising the proof generation or verification process.
- Scalability and Efficiency: ZKP architecture addresses scalability and efficiency concerns to enable practical implementation in real-world applications. This includes optimizing proof generation and verification algorithms, minimizing computational and communication overhead, and exploring techniques for batch processing or parallelization to handle large volumes of transactions or interactions.
- Integration and Adoption: ZKP architecture considers the integration of zero-knowledge proofs into existing systems and applications, as well as strategies for promoting adoption and usability. This involves providing developer-friendly tools and libraries, establishing standards and best practices, and educating stakeholders about the benefits and implications of zero-knowledge-proof technology.
Overall, zero-knowledge-proof architecture provides a framework for designing, implementing, and deploying secure and privacy-preserving systems and applications across various domains. By leveraging cryptographic techniques and protocols, ZKP architecture enables efficient and trustworthy interactions while safeguarding sensitive information and preserving individual privacy rights.
How Do Zero Knowledge Proofs Work?
A zero knowledge proof of knowledge works by having the verifier ask the prover to conduct a set of activities that can only be completed correctly if the prover is aware of the underlying information. When the prover is simply guessing about the outcome of these acts, the verifier’s test will almost certainly prove them wrong.
Shafi Goldwasser and Silvio Micali’s 1985 MIT article “The Knowledge Complexity of Interactive Proof-Systems” introduced zero-knowledge proofs. In this study, the researchers show that it is feasible for a prover to persuade a verifier that a particular claim about a data point is true while releasing no more information about the data.
WorkZKPs can be interactive, in which a prover persuades a particular verifier but must repeat the procedure for each individual verifier, or non-interactive, in which a prover provides a proof that can be confirmed by anybody with the same proof.
Different Zero-Knowledge Proof Types
ZKPs can be implemented in several ways, and each has trade-offs related to proof size, prover time, verification time, and other factors. Among them are:
-
zk-SNARKs
Simplistic non-interactive arguments of knowledge, or SNARKs, are compact and simple to validate. Utilizing elliptical curves, they produce a cryptographic proof that uses less gas than STARKS’s hashing function technique.
-
zk-STARKs
“Scalable transparent argument of knowledge” is what STARK stands for. STARK-based proofs are significantly quicker than SNARKs because they need less communication between the prover and the verifier.
-
PLONK
PLONKs, which stands for “permutations over Lagrange bases for oecumenical noninteractive arguments of knowledge,” employ a widely accepted configuration that works with any application and accommodates a sizable participant base.
-
Bulletproofs
Bulletproofs are brief, non-interactive proofs of zero knowledge that don’t need to be believed. Their purpose is to facilitate confidential cryptocurrency transfers.
Read Blog Post: Top 10 Real World Applications of Blockchain Technology
What are the Different Blockchain Use Cases of Zero-Knowledge Proof?
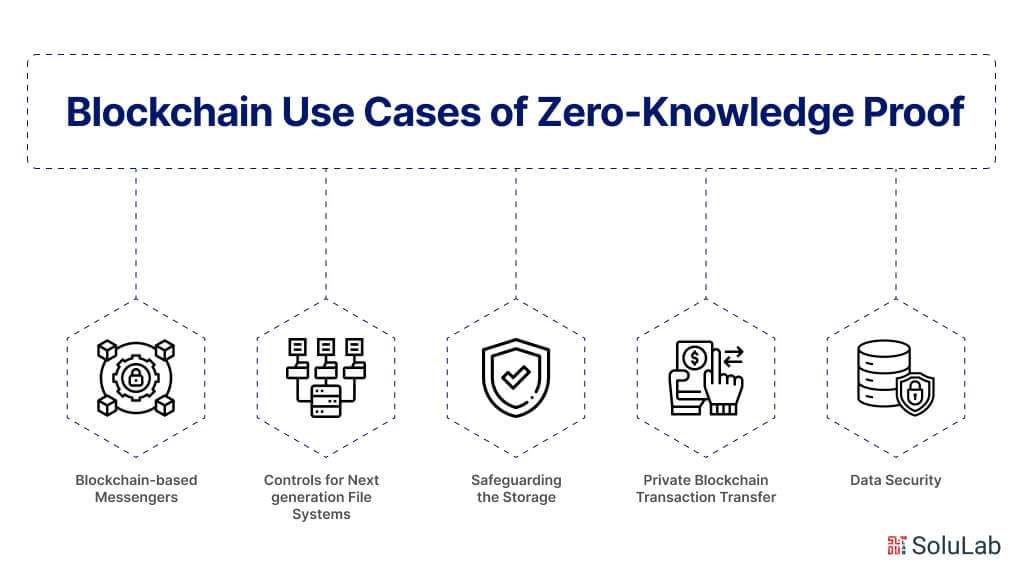
Zero-knowledge proofs (ZKPs) are cryptographic protocols that enable one party (the prover) to prove to another party (the verifier) that a statement is true without revealing any information beyond the validity of the statement itself. This concept has numerous applications across various domains due to its ability to enhance privacy, security, and efficiency. Here are some notable use cases of zero-knowledge proofs based on blockchain:
-
Blockchain-based Messengers
Even if today’s messengers claim to be encrypted, unencrypted blockchain has the potential to be the next great thing in technology. Blockchain technology and ZKPs can work together to build a value-added messaging platform that is safe for everyone, all while guaranteeing an unencrypted yet reliable solution.
-
Controls for Next-generation File Systems
Blockchain zero knowledge proof can assist in securing data and logins with several levels of protection. Because of this, ZKPs can provide significant barriers to data alteration and retrieval for hackers or manipulators.
-
Safeguarding the Storage
ZKPs incorporate a security protocol together with the data stored in the unit. Strong security measures on the access channels provide a smooth and extremely safe environment.
-
Private Blockchain Transaction Transfer
The main issue with private blockchain transactions is the many flaws in traditional processes. When ZKP and private blockchain transactions are successfully integrated, a strong, hacker-proof process may be created.
-
Data Security
Institutions like banks and hospitals that handle sensitive data have to protect it from outside access. When combined, ZKPs and blockchain may make data access impossible.
Check Blog Post: Role of Zero-Knowledge Proof in Blockchain and its Application
Benefits of Zero Knowledge Proof
Zero-knowledge proofs (ZKPs) offer a multitude of benefits across various domains, revolutionizing the way information is shared, transactions are conducted, and privacy is upheld. Here are some key benefits of zero-knowledge proofs:
- Enhanced Privacy: One of the most significant benefits of ZKPs is their ability to enable transactions and interactions without revealing unnecessary information. Users can prove the validity of a statement or transaction without disclosing any additional data beyond what is required, thus preserving their privacy and confidentiality.
- Improved Security: ZKPs contribute to enhancing security by reducing the risk of sensitive information exposure. Since only the necessary information is disclosed to verify a statement, the likelihood of data breaches or unauthorized access is minimized. This is particularly valuable in systems where privacy and security are paramount, such as blockchain networks and zero-knowledge authentication protocols.
- Data Minimization: Zero-knowledge proofs allow for data minimization, ensuring that only the essential information is shared or verified. This helps organizations comply with privacy regulations, such as GDPR, by reducing the collection and storage of sensitive data, thereby mitigating the risk of data misuse or unauthorized access.
- Efficiency: ZKPs can streamline processes by eliminating the need for extensive data exchange and verification. Since only the validity of a statement needs to be proven, unnecessary back-and-forth communication or data transmission can be avoided, leading to faster and more efficient transactions.
- Trust and Transparency: Zero-knowledge proofs promote trust and transparency among parties involved in transactions or interactions. By providing cryptographic assurances without revealing sensitive information, ZKPs enable parties to verify the integrity of statements or transactions, fostering trust in digital systems and reducing the need for intermediaries.
- Scalability: Zero-knowledge proofs offer scalability benefits, particularly in blockchain and decentralized systems. By enabling efficient verification of transactions or smart contracts without requiring full data disclosure, ZKPs can alleviate scalability challenges associated with processing large volumes of data on decentralized networks.
- Cross-Platform Compatibility: ZKPs can be implemented across various platforms and applications, making them versatile and interoperable. Whether it’s blockchain networks, zero-knowledge authentication protocols, or data-sharing systems, zero-knowledge proofs can be adapted to suit different use cases and technological environments, ensuring broad applicability and adoption.
- Innovative Applications: The benefits of ZKPs extend to enabling innovative applications and solutions that prioritize privacy, security, and user control. From privacy-focused cryptocurrencies to secure zero-knowledge authentication mechanisms and anonymous credential systems, zero-knowledge proofs pave the way for novel approaches to digital interactions and data management.
Zero-Knowledge Proof Applications

Zero-knowledge proofs (ZKPs) have a wide range of applications across various industries, offering solutions to challenges related to privacy, security, and efficiency. Here are some notable applications of zero-knowledge proofs:
-
Blockchain and Cryptocurrencies
ZKPs play a crucial role in enhancing privacy and confidentiality in blockchain development. Cryptocurrencies like Zcash and Monero leverage ZKPs to enable private transactions, where the sender, receiver, and transaction amount remain confidential while still ensuring transaction validity and integrity.
-
Identity Verification
ZKPs are used in identity verification processes to prove certain attributes or credentials without revealing unnecessary personal information. This can be applied in scenarios such as age verification, citizenship authentication, and access control systems, where privacy regulations and user confidentiality are paramount.
-
Authentication Protocols
Zero-knowledge proofs enhance authentication mechanisms by allowing users to prove their identity without disclosing sensitive information such as passwords or biometric data. ZKPs enable secure and privacy-preserving authentication protocols, reducing the risk of identity theft and unauthorized access to digital services.
-
Secure Data Sharing and Collaboration
ZKPs facilitate secure data sharing and collaboration among multiple parties while preserving confidentiality and privacy. In fields like healthcare and research, zero-knowledge proofs enable stakeholders to analyze sensitive data without accessing individual records, ensuring compliance with privacy regulations and protecting patient confidentiality.
-
Supply Chain Management
Zero-knowledge proofs are used in supply chain management to verify the authenticity and integrity of products or transactions without revealing proprietary information. ZKPs enable transparent and trustless supply chains, allowing stakeholders to track and verify the provenance of goods while protecting sensitive business data.
-
Anonymous Credentials
ZKPs enable the issuance and verification of anonymous credentials, where users can prove certain attributes without disclosing their actual identity. This can be applied in voting systems, access control mechanisms, and online services to ensure anonymity and privacy while still verifying user credentials.
-
Secure Voting Systems
ZKPs enhance the security and integrity of voting systems by enabling voters to prove the validity of their votes without revealing their choices. Zero-knowledge proofs ensure anonymity, prevent vote tampering, and enhance trust in electoral processes, making voting systems more secure and reliable.
-
Financial Transactions and Smart Contracts
Zero-knowledge proofs are utilized in financial transactions and smart contracts to enhance privacy and security. By leveraging ZKPs, parties can verify transactions or contract conditions without disclosing sensitive financial details, ensuring confidentiality and integrity in decentralized financial systems.
-
Digital Rights Management
ZKPs can be applied in digital rights management systems to protect intellectual property and prevent unauthorized access to copyrighted content. Zero-knowledge proofs enable content owners to prove ownership or entitlement to access rights without exposing sensitive information, reducing the risk of piracy and unauthorized distribution.
-
Compliance and Auditing
Zero-knowledge proofs facilitate compliance and auditing processes by enabling verifiable and transparent record-keeping without revealing sensitive data. ZKPs allow organizations to demonstrate compliance with regulations and standards while protecting confidential information from unauthorized access or disclosure.
Looking Ahead on the Future of Zero Knowledge Proof
The future of zero-knowledge proofs (ZKPs) is promising, with ongoing efforts aimed at advancing their capabilities, scalability, and applicability. Researchers are focused on enhancing efficiency and scalability to support large-scale applications like blockchain networks and decentralized finance platforms. This involves exploring optimization strategies and novel proof systems to reduce computational overhead and improve throughput.
Interoperability and standardization will become increasingly important as ZKPs gain traction across various domains and platforms. Efforts to define common protocols and formats will enable seamless integration of ZKPs into different systems, fostering interoperability and widespread adoption. Additionally, ZKPs have the potential to revolutionize privacy-preserving AI and machine learning by enabling secure computations over sensitive data while preserving confidentiality.
Decentralized identity and authentication systems stand to benefit from ZKPs, offering users a secure means to prove their identity or attributes without relying on centralized authorities. In the realm of blockchain, ZKPs can enable powerful and privacy-preserving smart contracts, ensuring confidential execution of contract logic and compliance with regulations. As quantum computing rises, research into post-quantum secure ZKPs will be crucial for long-term security and resilience.
Looking ahead, increased adoption of ZKPs in real-world applications is expected, spanning industries such as finance, healthcare, and government services. Efforts to deploy ZKPs in practical use cases, address regulatory concerns, and educate stakeholders about their benefits will be essential. ZKPs, as part of a broader ecosystem of privacy-enhancing technologies, enhance privacy, security, and trust in the digital age.
Final Words
Zero knowledge proofs will transform the way we think about data management, allowing users to fulfill compliance requirements or validate particular facts without revealing personal information or trade secrets. We are already witnessing tremendous development in the blockchain area, with zero-knowledge technologies assisting to expand the ecosystem and increase user privacy. Finally, improving the privacy, security, and effectiveness of digital systems will have far-reaching implications for blockchain networks, voting systems, supply chains, and a variety of other businesses.
SoluLab, with its expertise in blockchain technology and cryptography, is well-positioned to provide comprehensive solutions and support in implementing zero-knowledge proofs (ZKPs). Whether it’s designing and developing privacy-preserving blockchain applications, integrating ZKPs into existing systems, or conducting research and consulting on cryptographic protocols, SoluLab offers tailored services to meet the unique needs of businesses and organizations. With a team of skilled developers and consultants, SoluLab ensures efficient and secure implementation of ZKPs, enhancing privacy, security, and trust in digital interactions. Contact us today to explore how we can empower your organization with zero-knowledge proofs and elevate your digital initiatives to the next level.
FAQs
1. What is zero-knowledge proof (ZKP) and how does it work?
Zero-knowledge proof (ZKP) is a cryptographic protocol that allows one party (the prover) to prove to another party (the verifier) that a statement is true without revealing any additional information beyond the validity of the statement itself. In essence, ZKP enables verification of the truth of a statement without disclosing any underlying data or knowledge.
2. What are the main applications of zero-knowledge proof?
Zero-knowledge proofs have diverse applications across various domains. Some notable applications include enhancing privacy in blockchain and cryptocurrency transactions, enabling secure and privacy-preserving authentication mechanisms, facilitating confidential data sharing and collaboration, and verifying the integrity of sensitive computations in areas like AI and machine learning.
3. How does zero-knowledge proof benefit blockchain technology?
In blockchain technology, zero-knowledge proofs play a crucial role in enhancing privacy, scalability, and security. By enabling confidential transactions, ZKPs improve privacy for participants in blockchain networks, ensuring sensitive financial information remains confidential. Additionally, zero-knowledge proofs allow for more efficient and scalable blockchain protocols by reducing computational overhead and transaction verification times.
4. Can zero-knowledge proofs be used for identity verification?
Yes, zero-knowledge proofs can be used for identity verification in a privacy-preserving manner. By allowing individuals to prove certain attributes or credentials without revealing their actual identity, ZKPs enable secure and privacy-enhanced authentication mechanisms. This has applications in decentralized identity systems, access control mechanisms, and secure authentication protocols.
5. Are there any real-world examples of zero-knowledge proof being used?
Yes, there are several real-world examples of zero-knowledge proof being used across various industries. For instance, Zcash, a privacy-focused cryptocurrency, utilizes zero-knowledge proofs to enable private transactions, where the sender, receiver, and transaction amount remain confidential. Additionally, organizations in healthcare, finance, and supply chain management are exploring the use of ZKPs to enhance privacy, security, and efficiency in their operations.






